CYBERSECURITY FOR CRITICAL INFRASTRUCTURE
Fractal EMS was designed for Critical Infrastructure Protection. Fractal EMS is built on the NIST 800-53 framework and applies best practices of policies, architecture, and operational processes to satisfy the requirements of our most security-sensitive customers. Fractal EMS utilizes a comprehensive, integrated approach to ZTA (Zero Trust Architecture) within our cybersecurity IT/OT networks. We adhere to proven methodologies and apply best practices. Our position is to provide a ``Zero Trust`` framework and architecture to meet or exceed Industrial Controls Systems cybersecurity requirements, including personnel, hardware, and software. Fractal EMS has an in-house team of cybersecurity and IT specialists to provide an architecture that meets project requirements.
NIST CYBERSECURITY FRAMEWORK 2.0
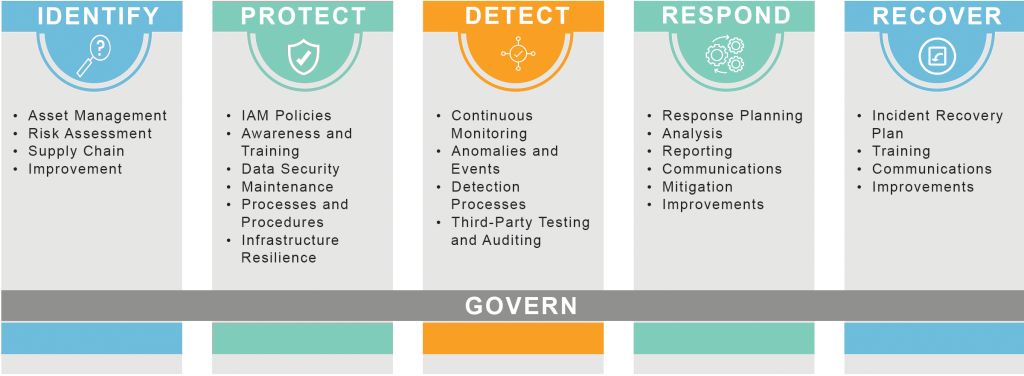
FRACTAL EMS CYBSERCURITY PROCESSES
- MFA authentication for access, communications, and account management using industry-standard protocols
- Layering and segmentation of devices and encryption, including endpoints, firewalls, and intrusion detection systems
- Server-to-cloud connectivity using MQTT and TLS 1.3 with digital certificate authentication
- Real-time monitoring of appliances, operating system (OS), configuration, firmware, common vulnerabilities, and exposures (CVE)
- Operation, engineering, commissioning malware, anti-virus, ransomware, spyware, and malicious code protection and mitigation
- Data retention and recovery training and testing
- Inventory control of network hardware and software assets
- Internal policies, procedures, and accountability
- Incident response management
- Penetration and vulnerability testing
- Change management that defines what controls, standards, and requirements are needed within documents, data, configuration, and escalation
- Account management to identify and authenticate users, devices, and software within the architecture
- Public Key Infrastructure (PHI) authentication and management
- Network and application distributed denial of service (DDoS) protection
- System use notification
- Auditable log, resource, and management to include historical data retention
- Data retention and recovery training and testing
- Corporate Security Awareness: phishing testing, cybersecurity training, email and web browser protection, internal and external communications protections
REQUEST A PROPOSAL
Request a proposal today and see how we can make your project and bids more competitively priced.
